Risk assessment for enterprise networks
News & Insights
10 Min Read
Risk Assessment for Enterprise Networks: A Comprehensive Guide Risk assessment for enterprise networks is a critical process for identifying, evaluating, and managing risks that can potentially disrupt or compromise an organization's IT infrastructure and operations. As cyber threats become more sophisticated, enterprises must proactively assess vulnerabilities and mitigate risks to maintain network integrity, confidentiality, and availability. In this guide, we will walk through the steps of conducting a risk assessment for enterprise networks, explore the key components involved, and highlight strategies for managing identified risks.
Why is Network Risk Assessment Important?
A network risk assessment helps enterprises understand the risks that can affect their network infrastructure, including:
Cybersecurity Threats: External and internal threats such as hacking, malware, ransomware, phishing, and data breaches.
System Downtime: Network failures that can lead to operational interruptions.
Data Loss: Loss of sensitive or critical business data, whether due to breaches, system failures, or disasters.
Compliance Violations: Non-compliance with industry regulations such as GDPR, HIPAA, or PCI-DSS, which can result in penalties.
Reputation Damage: Cyber incidents can severely damage the company’s reputation and erode customer trust.
By performing a thorough risk assessment, businesses can identify these threats, evaluate their potential impact, and take action to reduce or eliminate them.
Steps in Conducting a Network Risk Assessment
1. Define the Scope of the Assessment
The first step is to establish the scope of the risk assessment by identifying which parts of the enterprise network will be evaluated. This typically includes:
Network Infrastructure: Servers, routers, switches, firewalls, etc.
Data Storage: Databases and file systems where sensitive data is stored.
Applications: Software systems, both internal and external-facing.
Users: Access points such as devices, terminals, and remote access connections.
Understanding the scope ensures that the assessment is thorough and covers all critical components that might be exposed to risk.
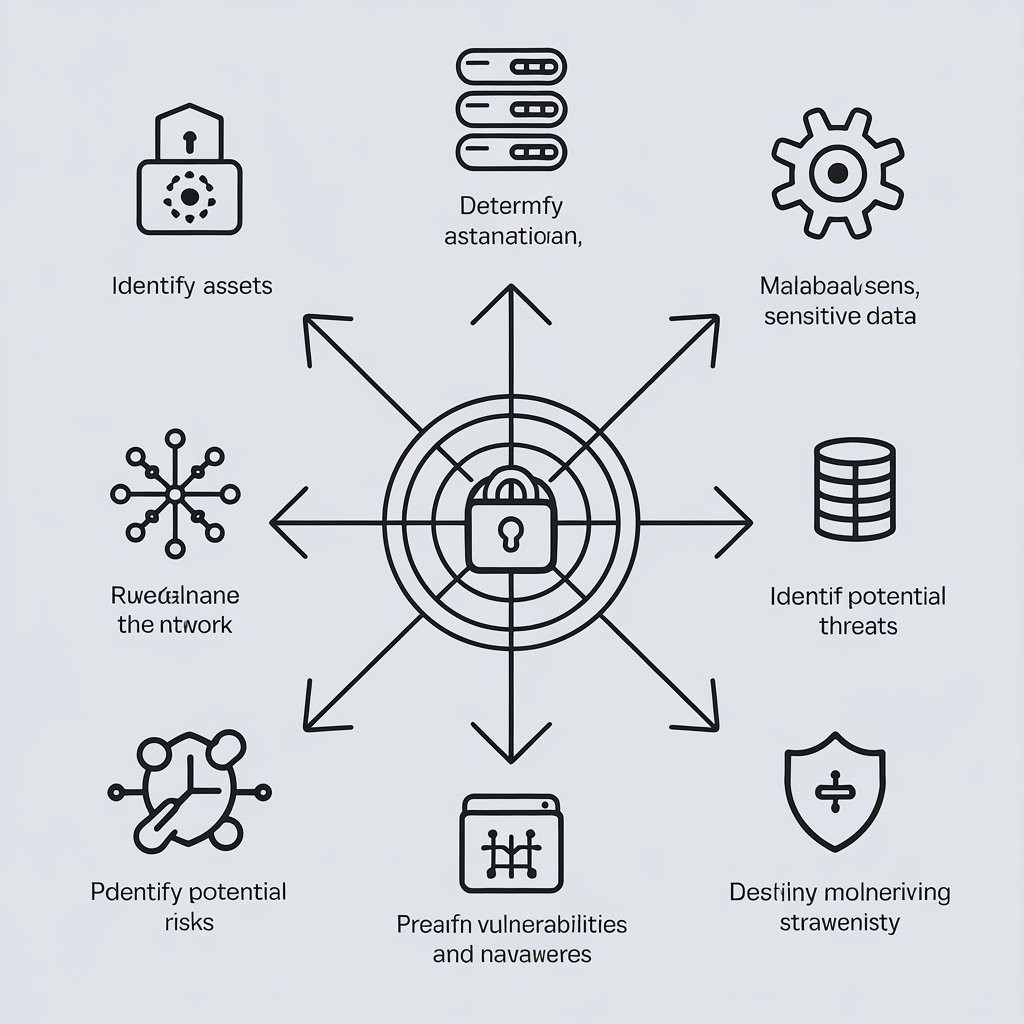
2. Identify Assets
List all the assets in the network infrastructure, including:
Hardware: Servers, workstations, network devices, and mobile devices.
Software: Operating systems, applications, tools, and any third-party services.
Data: Sensitive data such as customer information, financial records, intellectual property, etc.
People: Employees, contractors, and other users with access to the network.
These assets must be properly protected, so identifying and classifying them based on sensitivity and criticality is essential for assessing risk.
3. Identify Potential Threats
Identify and document the potential threats that could compromise the network. Common network threats include:
External Threats: Hackers, cybercriminals, nation-state actors, and other external entities.
Internal Threats: Employees, contractors, or trusted users who intentionally or unintentionally compromise the network.
Natural Disasters: Events such as floods, earthquakes, fires, or power outages that could affect the network infrastructure.
System Failures: Hardware or software malfunctions that could cause network outages or data loss.
Threats can evolve over time, so it’s essential to stay up to date on emerging risks and include them in the assessment.
4. Identify Vulnerabilities
Once potential threats are identified, the next step is to identify the vulnerabilities in the network that these threats could exploit. Some common network vulnerabilities include:
Weak Passwords: Poor password policies that can lead to unauthorized access.
Unpatched Software: Outdated software or hardware that may have known vulnerabilities.
Unsecured Communication Channels: Lack of encryption in communications that can expose sensitive data.
Misconfigurations: Incorrect network settings or improperly configured security controls.
Unsecured Endpoints: Devices such as laptops, mobile phones, and IoT devices that lack adequate security protections.
Vulnerability scanning tools and penetration testing can be used to identify these weaknesses in the network.
5. Assess the Impact and Likelihood of Threats
Evaluate the potential impact and likelihood of each identified threat exploiting a vulnerability. This involves considering:
Impact: What would happen if the threat were to occur? Could it result in data loss, financial damage, reputational harm, or operational downtime?
Likelihood: How likely is the threat to occur? Is it a common attack vector, or is it a rare risk?
A risk matrix can be used to assess and prioritize these factors. For example, risks that have both high impact and high likelihood should be addressed first.
6. Evaluate Existing Controls
Next, assess the existing security controls and measures that are currently in place to mitigate the risks. These controls may include:
Firewalls: Protect the network perimeter by blocking unauthorized access.
Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for suspicious activity and block potential attacks.
Encryption: Protect data in transit and at rest from unauthorized access.
Access Controls: Restrict network access to authorized personnel and devices only.
Backup Systems: Ensure critical data is regularly backed up to facilitate recovery in case of a breach or disaster.
Evaluate the effectiveness of these controls in reducing the identified risks. If gaps or weaknesses are discovered, additional measures may be needed.
7. Risk Mitigation Strategies
Based on the assessment, develop a risk mitigation plan that outlines how to reduce or eliminate identified risks. Common strategies include:
Risk Avoidance: Eliminate the activities or processes that pose the highest risk (e.g., decommissioning vulnerable legacy systems).
Risk Reduction: Implement controls to reduce the likelihood or impact of a risk (e.g., applying patches, strengthening firewalls).
Risk Sharing: Transfer the risk to another entity, such as by purchasing cyber insurance or outsourcing certain IT functions.
Risk Acceptance: Accept risks that are minor or unavoidable, but ensure they are continuously monitored.
Each risk should be addressed with the appropriate mitigation strategy based on the organization’s risk tolerance.
8. Implement Risk Mitigation Measures
After determining the appropriate mitigation strategies, implement the necessary measures. This may involve:
Upgrading network hardware or software to more secure versions.
Deploying additional security tools (e.g., next-gen firewalls, advanced endpoint protection).
Enhancing user training to reduce the risk of social engineering or phishing attacks.
Implementing multi-factor authentication (MFA) to secure access to critical systems.
Conducting regular vulnerability scanning and penetration testing.
9. Continuous Monitoring and Review
Cyber threats and vulnerabilities evolve over time, so risk assessment is not a one-time activity. Continuously monitor the network for new threats and vulnerabilities, and regularly review the effectiveness of your risk mitigation measures.
Regular Audits: Conduct periodic risk assessments to ensure controls remain effective.
Incident Monitoring: Use Security Information and Event Management (SIEM) systems to monitor for potential security incidents.
Continuous Training: Provide ongoing cybersecurity training for employees to keep them aware of new threats.
Tools for Network Risk Assessment
Several tools and techniques can help organizations conduct a thorough network risk assessment:
Vulnerability Scanners: Tools like Nessus, OpenVAS, or Qualys can automatically scan the network for vulnerabilities.
Penetration Testing: Ethical hacking tools such as Kali Linux and Metasploit can be used to simulate real-world attacks and identify weaknesses.
Network Monitoring Solutions: Solutions like Nagios or SolarWinds help track network performance and detect anomalous activities.
Risk Management Frameworks: Frameworks like NIST, ISO 27001, and FAIR (Factor Analysis of Information Risk) provide structured approaches for conducting risk assessments. audit3aa
Join our newsletter list
Sign up to get the most recent blog articles in your email every week.